Ad Vulnerability assessment and penetration testing are ways to discover weak spots. While youre examining your network traffic you should look for Link-Local Multicast Name Resolution LLMNR and ensure that its disabled if possible.

7 Best Network Penetration Testing Tools In 2022 Demos Pros Cons
At least make an attacker have to do a bit of work.
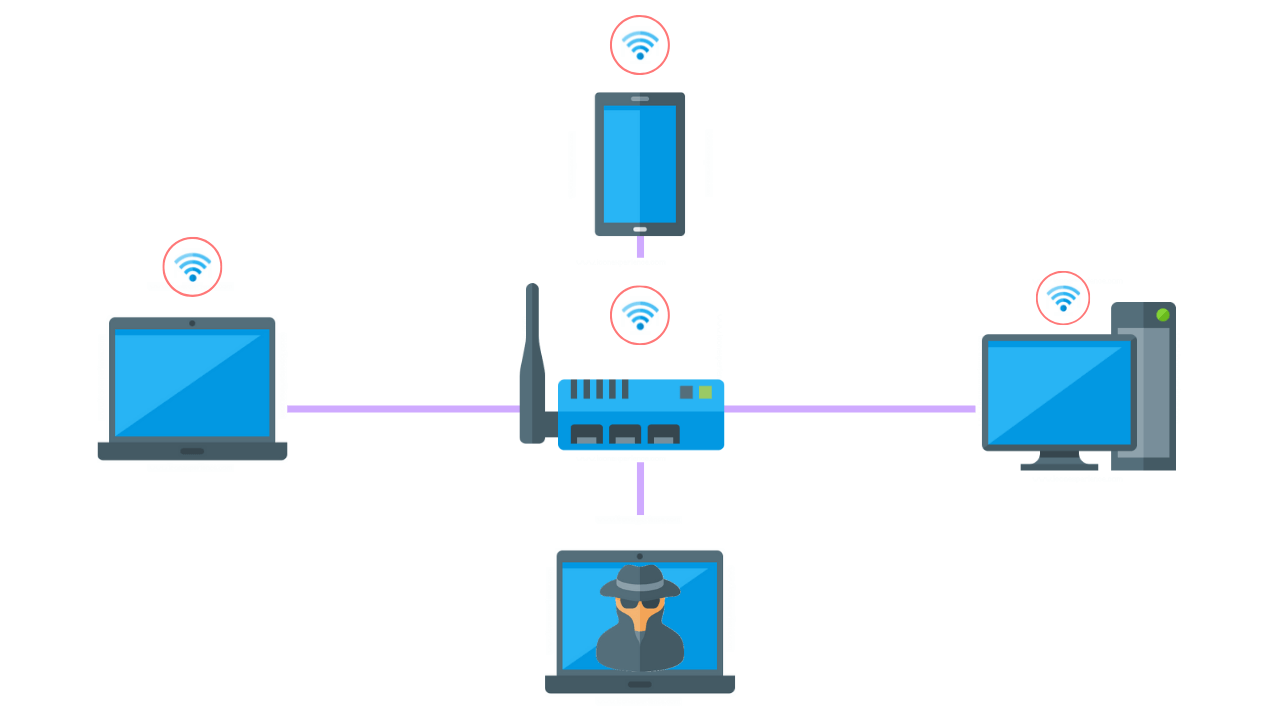
. Would you like to receive a quote for our vulnerability scan and pentesting services. While replies to SMishing attempts may reveal sensitive information links front. Ad Vulnerability assessment and penetration testing are ways to discover weak spots.
Step 2 of this network penetration testing checklist. Would you like to receive a quote for our vulnerability scan and pentesting services. You should also check with your ISP.
Creating a clone of it will prevent you from re-installing it again and again. The first thing they are going to do is port scan your IP address and find out what youve got running if anything. CNAME Makes the domain name to another domain name.
Discovery After your organization has. Network Pentest Checklist for Phase 2. A targeted pentest is one of the best ways to ensure all network compliance requirements are being met.
Ii Configure the exploit with remote IP address and remote port number. Expect everything else to be filtered. A home pentesting lab is a good way to hone skills while staying out of legal trouble.
SMishing realistically only has two attack vectors for a pentester. Extending your Wi-Fi coverage by installing additional Wireless Access Points or a more powerful access point. If you dont know any such person then grab a trusted friend who is non-technical and ask them to run a couple of small tests on your.
Then verify that it is your home. The first thing we need to do is connect the box to a WiFi. By clicking the network icon and holding down the WiFi.
The wireless network can be turned on and off by right-clicking a network icon in the corner and selecting Enable WiFi or Disable WiFi. Expect to find only the ports you know you have explicitly opened open. After collecting all the information you can about your target network its time to use this information for something dicey.
Advanced IP Scanner is one of the programs that undoubtedly supports this fundamental step of Network PenTesting. In case you have a trusted external pen. Iii Pick a payload.
This step is very helpful in case your VM gets corrupt. I Pick which exploit to use. I highly recommend you do a similar inspection on any device you put on your network.
You can create a clone by Right clicking on the Virtul machine instance in. Replying to a text or clicking on a link. And not that this makes a huge difference but do not use the standard port for your game app.
First run a full scan against your home IP address. Click on the Windows icon in the far left of your taskbar followed by Settings the cog symbol that appears just above it. If youre not running anything and all ports are closed the attack is basically done unless.
UDP Scanner top 1000 ports 3. TCP Scanner ports 1-65535 2. Depending on government regulations and their own operating policies they could be required to block your pentest actions if detected or cancel your.
Hacking into other peoples computers and networks is illegal without prior consent but its perfectly legal to set up your own lab that mimics someone elses environment and then pentest your. Or you can extend the Wired. Those exploits would need to run over the port you have open.
Lets begin shall we. You can extend your home network by. But if you try to find out vulnerabilities in devices present in the test network then you should arrange some pen testing tool on your test network.
Below we have explained how to ensure it is turned on. When youre ready to start include the following tools in your scan template with the configuration below. Hacking into other peoples computers and networks is illegal without prior consent but its perfectly.
Iv Configure the payload with local IP address and local port number. First of all you can try to get a technical friend to help. Weidman said that you can capture password.

Ngrok For Penetration Tester S Exposing Your Local Pen Test Tools By Alexis Rodriguez Geek Culture Medium

How To Scope A Network Penetration Test Pentester Tips Cobalt
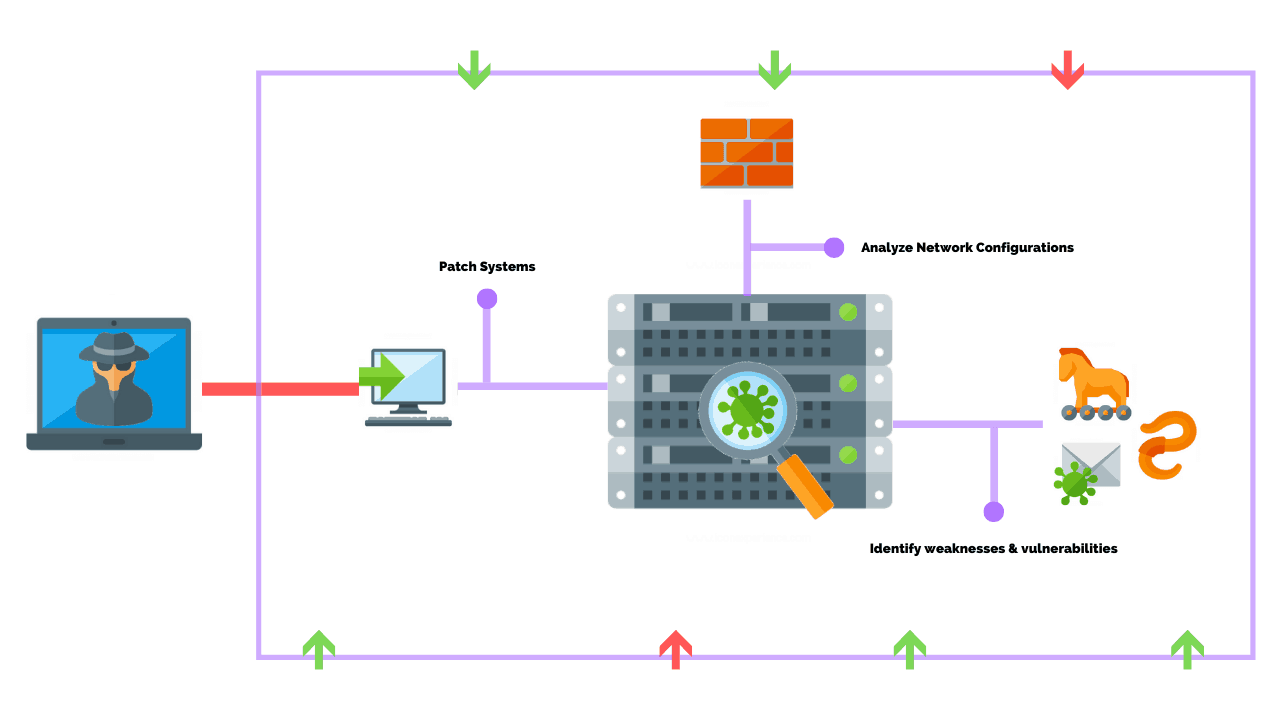
How To Perform A Successful Network Penetration Test Purplesec

How To Perform A Successful Wifi Penetration Test

Hacking Your Home Pen Testing Your Local Network By Aliaksandra Havia Medium



0 comments
Post a Comment